Image Encryption Technologies and Applications
ZHOU Yi Cong
University of Macau
5G is around the corner! Enormous images and videos are uploaded to the Internet or transmitted over public channels in Macau, China, and all over the world. These images and videos may contain private, sensitive, or even classified information. Providing security to these images and videos has become an urgent and critical issue for individuals, organizations and governments. Image encryption is a technique to encrypt images and videos by transforming them into an unrecognized format. Existing image encryption methods may suffer from security defects or heavily computational burden. This research project develops innovative chaotic maps and systems and their corresponding image encryption algorithms, proposes several image encryption concepts and their implementation schemes, and applies them to the security areas of reversible data hiding and secret image sharing. The outcomes of this research project have benefited to the research community of Macau and China.
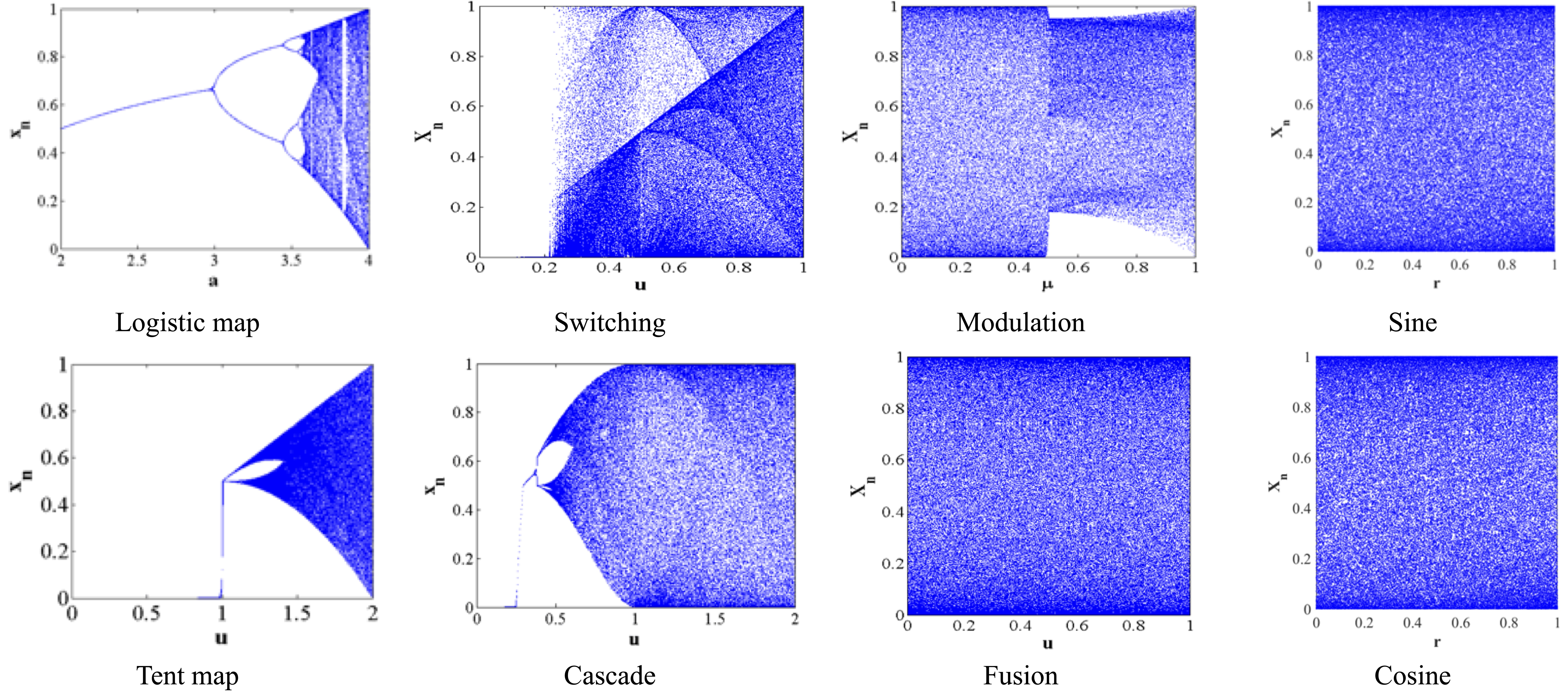
Fig 1 Bifurcation diagrams of chaotic maps generated by different chaotic systems. Their chaotic regions are plotted in blue. The 1st column shows existing Logistic and Tent maps. Using Logistic and Ten maps as seed maps, different chaotic systems are able to generate new chaotic maps in the 2nd -- 4th columns. As can be seen, all chaotic maps in the 2nd -- 4th columns have much larger chaotic ranges and better chaos performance than their seed maps in 1st column. This benefits the security and encryption performance of their corresponding image encryption algorithms.
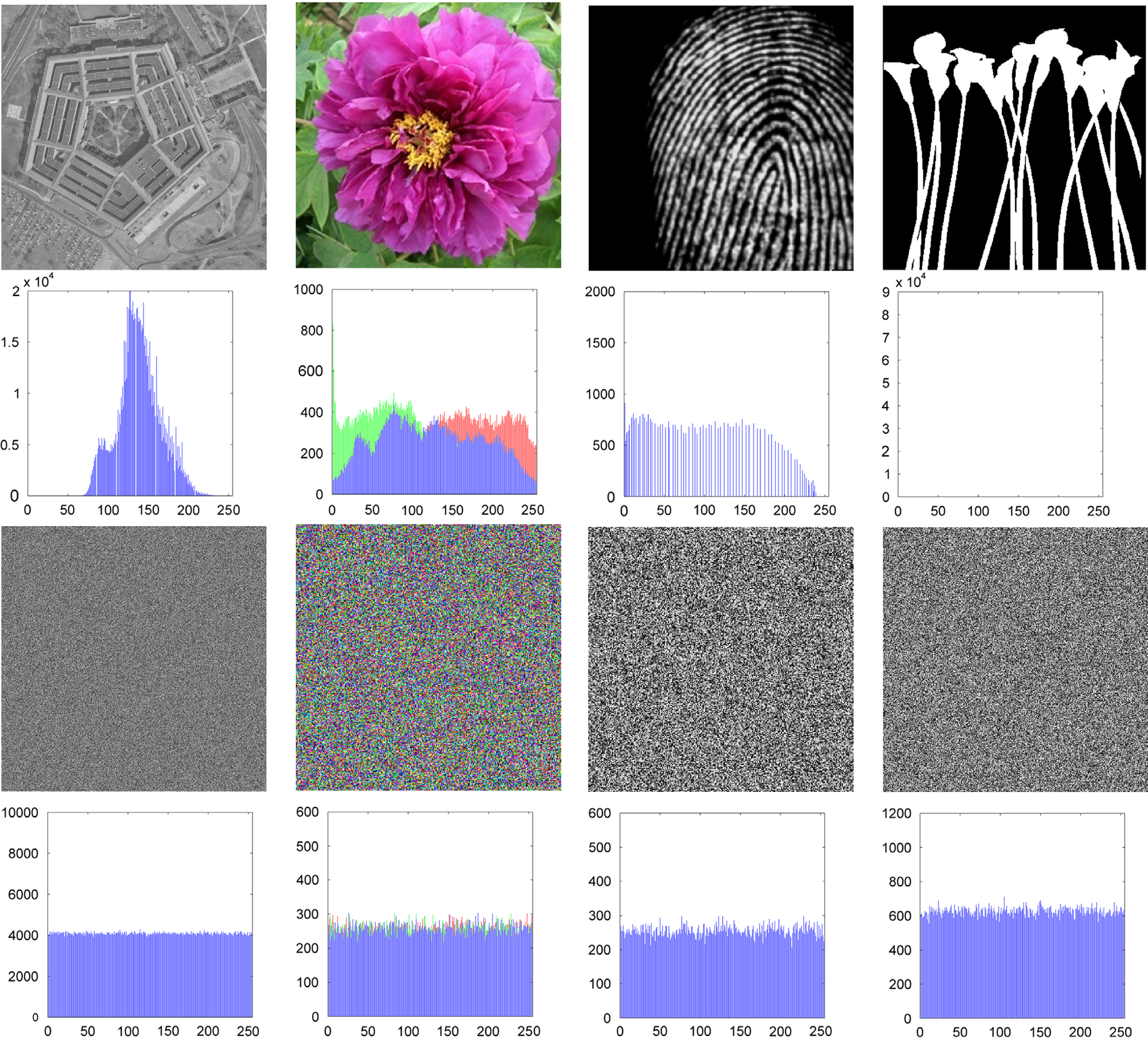
Fig 2 Encryption results of different types of images. The original and encrypted images are shown in the 1st and 3rd rows, respectively. These images are the grayscale, color, biometric, binary images. Their histograms are plotted in the 2nd and 4th rows.


